Features
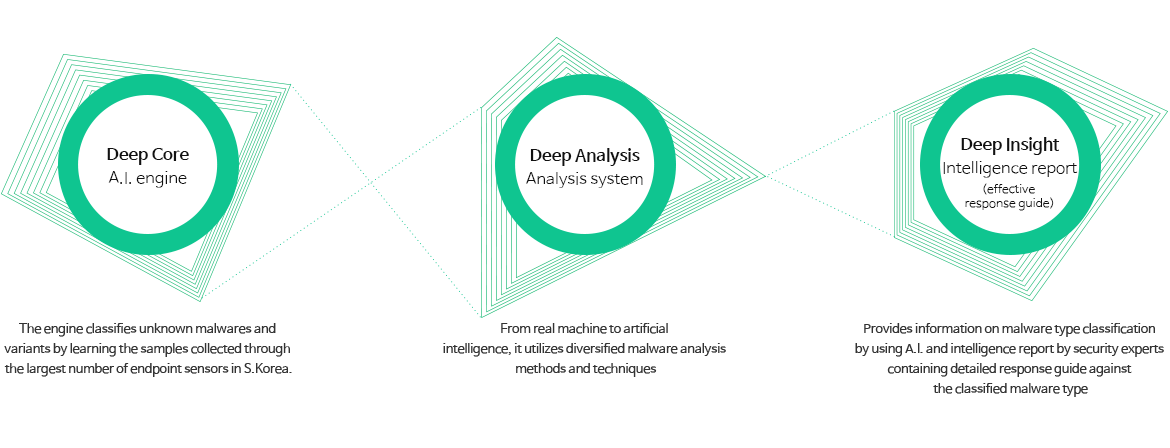
3 core elements of Threat Inside
-
-
Deep Core
-
Enhances A.I. performance by self-training of real-time detected malwares
Minimizes false detection rate through double-checking process by the false-positive verification system
Real-time response with the notably faster analysis than static/dynamic analysis
Provides optimized services for security environment through close cooperation with S. Korean and international organizations and enterprises
-
Deep Analysis
-
Implements the full range of threat analysis on from the real machines to artificial intelligence
Provides not only features and behaviors of the malware but also the intelligence of its related threats
Provides level-based analysis information for corporate IT managers and malware analysis experts
-
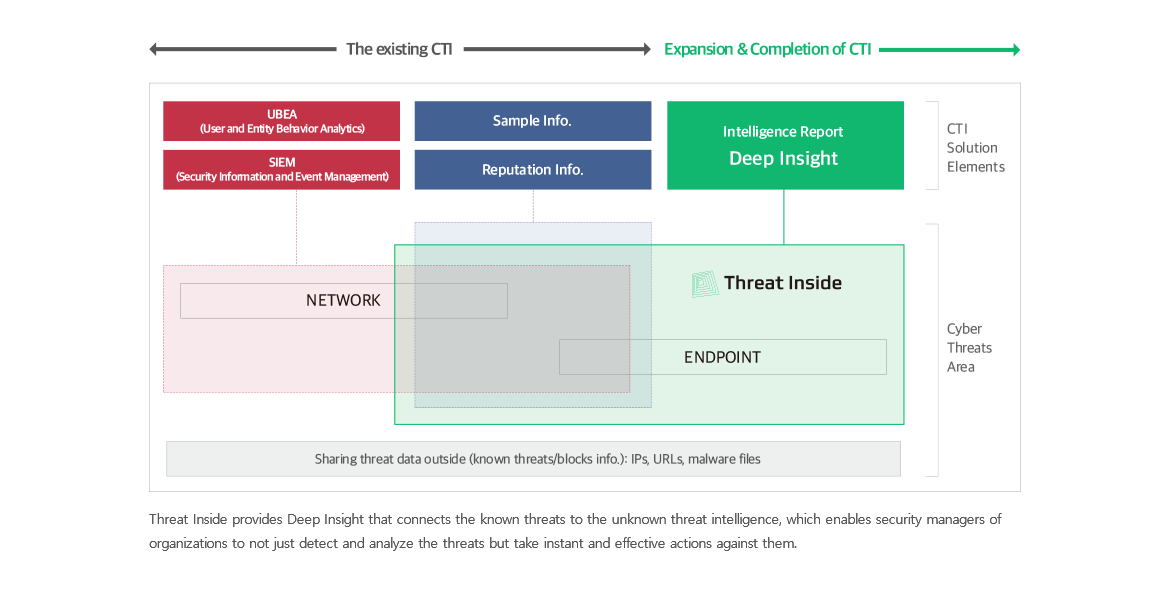
Deep Insight
-
Classifies automatically the malware types through A.I. analysis of Deep Core
Provides Deep Insight (intelligence report) containing from main features of the malware, manual analysis result, to the effective response guide
Provides the basis information and detailed insights regarding APT attacks such as detected ransomwares
-